.svg)
.svg)


Identify breaches before they become public, allowing for swift action to prevent further damage.

Reduce the risk of data leaks that can erode customer trust and tarnish your brand's image.

Prevent financial losses from fraudulent activities and ransomware attacks by detecting threats early.

Demonstrate proactive risk management to meet data protection regulations like GDPR or HIPAA, avoiding potential fines and legal repercussions.

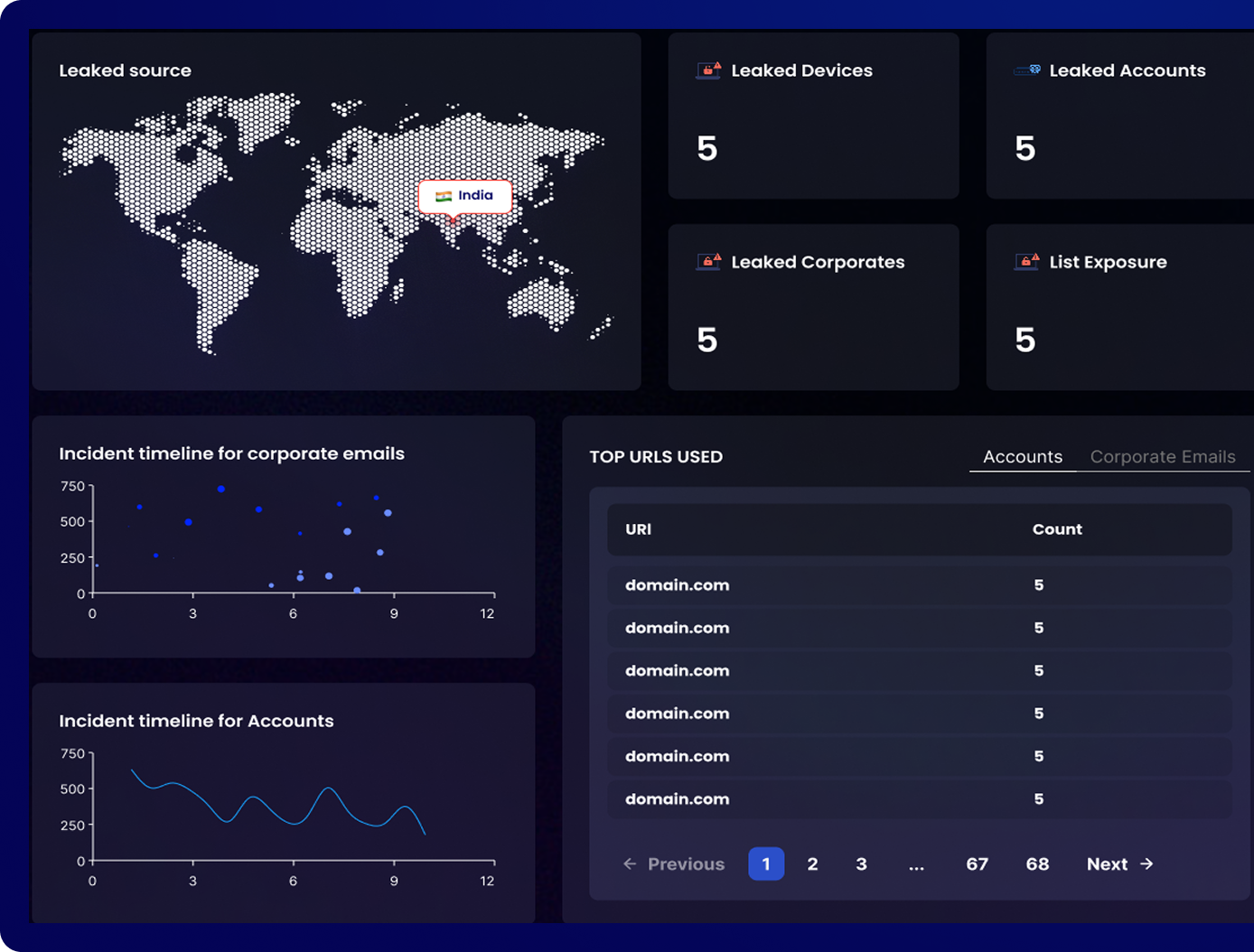
We go beyond simple database leaks by directly monitoring malicious networks, providing the most extensive data to detect the initial point of compromise.
We deliver the exact date of the breach, sourced directly from the compromised device’s system.
Identify the operating system of the affected device, ensuring precise and actionable insights.
We extract and report the username associated with the compromised device.
Hostname data of the breached device is collected and shared for better tracking and mitigation.
IPv4 and IPv6 addresses of compromised devices are provided for full visibility and threat assessment
We locate and disclose the exact malware path that infected the device, aiding in immediate response and cleanup.
We identify the installed antivirus solutions on the compromised device to assess vulnerabilities.
Compromised URLs, usernames, and passwords extracted from victims’ browsers are reported, allowing swift credential resets and damage control.
